Binary Vulnerability Analysis
About Binary Vulnerability Analysis
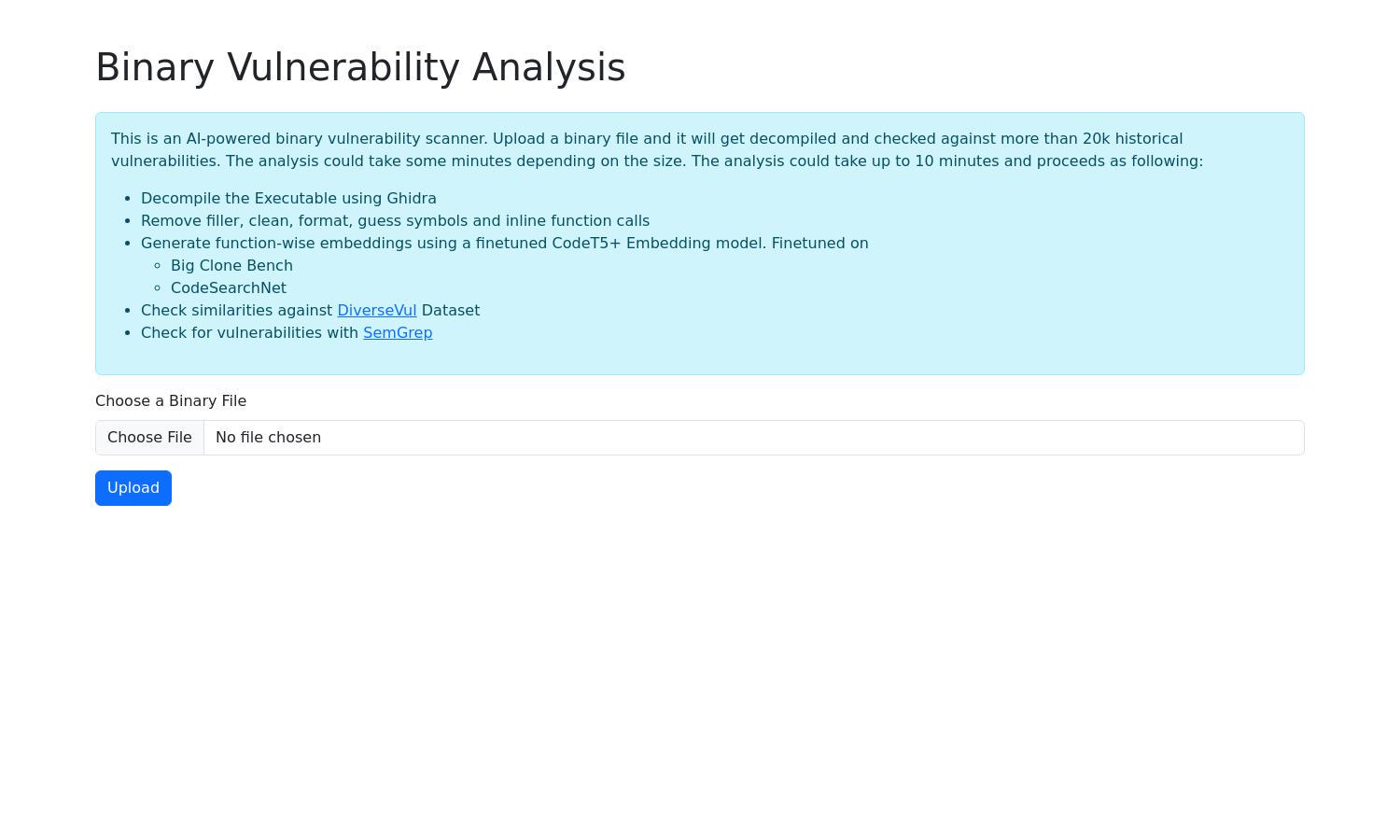
Binary Vulnerability Analysis is a groundbreaking platform that empowers developers to secure applications by detecting vulnerabilities in binary files. Using advanced AI and machine learning techniques, it decompiles executables and identifies over 20k historical vulnerabilities, helping users enhance their security posture effortlessly.
Binary Vulnerability Analysis offers various pricing plans tailored for individuals and businesses. Each tier provides enhanced features for vulnerability scanning, decompilation, and comprehensive reporting. Users can access exclusive discounts, highlighting the advantages of upgrading for more in-depth analysis while maximizing security and efficiency.
The user interface of Binary Vulnerability Analysis is designed for simplicity and efficiency, ensuring a seamless experience. Easy navigation allows users to upload binaries and view results effortlessly. The layout features intuitive controls and clear visualization of analysis results, making security assessments stress-free and effective.
How Binary Vulnerability Analysis works
Users begin with Binary Vulnerability Analysis by easily uploading their binary files, which are then decompiled using Ghidra. The platform identifies and removes any filler, cleans up formats, and makes intelligent guesses on symbols and inline functions. Next, the files undergo sophisticated analyses, cross-referenced with a diverse dataset of vulnerabilities. This user-friendly process ensures efficient and thorough vulnerability scanning for any application.
Key Features for Binary Vulnerability Analysis
AI-Powered Binary Scanning
Binary Vulnerability Analysis utilizes an advanced AI model for meticulous binary scanning. This key feature efficiently identifies vulnerabilities, ensuring that developers secure their applications against a backdrop of over 20,000 historical vulnerabilities, significantly enhancing user trust and application safety.
Comprehensive Decompilation Process
The comprehensive decompilation process in Binary Vulnerability Analysis transforms uploaded binaries using Ghidra, refining and cleaning files. This unique attribute enables users to easily identify vulnerabilities, promoting a deeper understanding of potential security risks and maximizing application safety with thorough analysis.
Vulnerability Cross-Referencing
Binary Vulnerability Analysis excels in vulnerability cross-referencing by leveraging a diverse dataset. This crucial feature allows users to match detected vulnerabilities against extensive historical records, ensuring a thorough examination and aiding developers in addressing security risks effectively and timely.